Katalyst Network Group Blog
Resources and insights for technology and executive leaders

Are You as Secure as You Think? Unpacking the Gaps in Today’s Cybersecurity Landscape
Are You as Secure as You Think? Unpacking the Gaps in Today’s Cybersecurity Landscape Katalyst If you’ve ever wondered, “Are

Are You the Imelda Marcos of Technology Providers?
Are You the Imelda Marcos of Technology Providers? Jesse White Imelda Marcos was famously known for owning over 3,000 pairs

The IT Turnover Crisis: Why Managed Services Are Your Safety Net
The IT Turnover Crisis: Why Managed Services Are Your Safety Net Katalyst We hear it from clients all the time:

Katalyst Network Group Named to CRN Solution Provider 500 List for 2025
Katalyst Network Group Named to CRN Solution Provider 500 List for 2025 Katalyst Charlotte, NC, May 27, 2025—Katalyst Network Group,

Shadow IT Is Growing — Here’s How to Regain Control Without Slowing Innovation
Shadow IT Is Growing — Here’s How to Regain Control Without Slowing Innovation Katalyst Across industries, we’re seeing a growing

Upcoming Microsoft Entra Connect Update – Action Required by April 7, 2025
Upcoming Microsoft Entra Connect Update – Action Required by April 7, 2025 Katalyst Microsoft has announced a critical hardening update
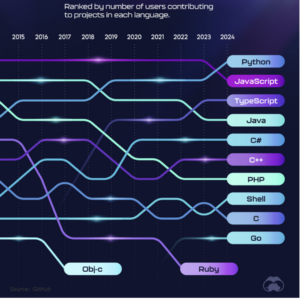
The Evolution of Programming Languages & Why It Matters In Your Business
The Evolution of Programming Languages & Why It Matters In Your Business Jesse White One thing I’ve noticed in my

The Hidden Cost of Cybersecurity Gaps
The Hidden Cost of Cybersecurity Gaps Katalyst The Hidden Cost of Cybersecurity Gaps: How to Avoid Losing Business A new

Optimizing Hybrid Meetings: How the City of Southport Improved Public Accessibility
Optimizing Hybrid Meetings: How the City of Southport Improved Public Accessibility Katalyst City government meetings play a crucial role in

