3 Cyber Threats Every C-level Leader Should to Be Aware of
Jesse WhiteCybersecurity is a bit like one long at-bat in baseball.
Consider Ted Williams, the legendary MLB player. He’s known for being the only player in MLB history to bat above 0.400, meaning he had a 4 in 10 chance of putting the ball in play. His 1941 record still stands untouched today.
Interestingly though, he also held the record for the most foul balls, because he would knock some pitches to the side while he patiently waited for a pitcher to make a mistake and give him the perfect pitch.
In cybersecurity, the "batter" has to hit every pitch, regardless of whether it's in their sweet spot. Your security tools might protect your most critical assets, but you still have to pay attention to everything else.
Like a skilled batter, executive leaders and cybersecurity teams need to be aware of the speed, appearance, and origin of incoming threats.
1. Third-party risk through APIs
APIs enable different software applications to communicate with each other, providing a flexible and efficient way to integrate systems and services.
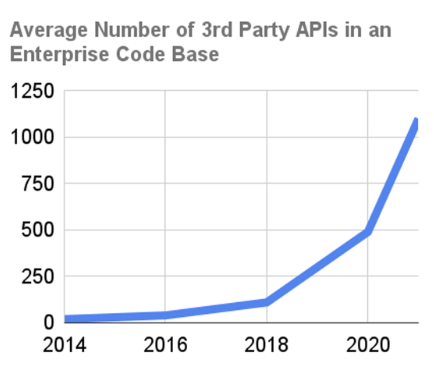
The past few years have seen a massive spike in API usage, driven by the rapid growth of digital transformation, cloud computing, and mobile applications. This powers much of our connected business world today.
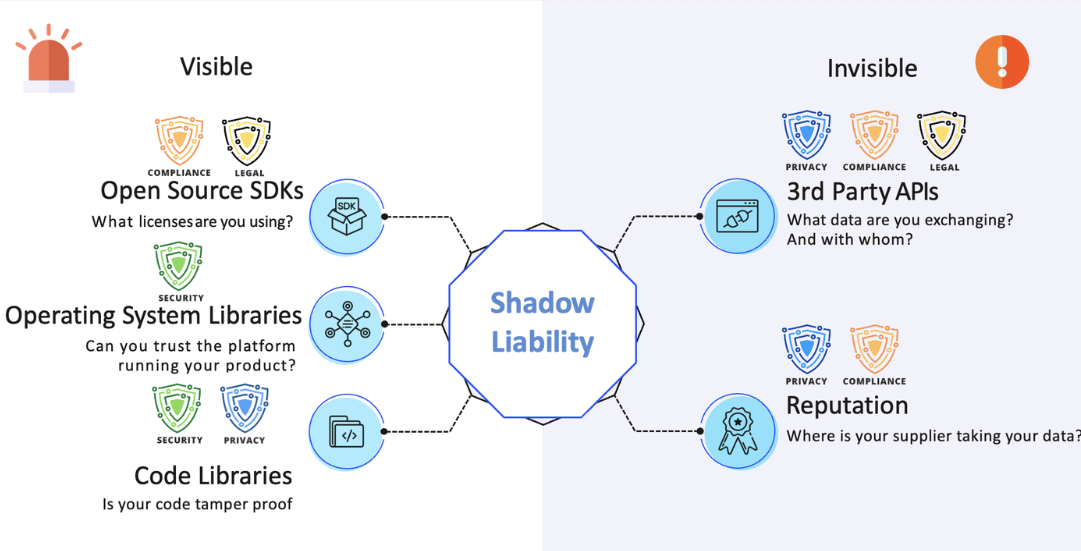
However, the widespread adoption of APIs also creates new security challenges and increased risk exposure for businesses in several ways. APIs are often built using open source software, which can still be vulnerable to security risks (Google is pushing to increase the security of open source software).
Here are a few examples of how this creates risk for your company that could potentially impact your operation:
- Inadequate security practices: Weak API security measures, such as poor authentication, access controls, and encryption, can leave organizations susceptible to data breaches and other security incidents. Third-party APIs aren’t always secure.
- Complex API ecosystems: With so many interdependent links between various APIs, it becomes more challenging for businesses to maintain visibility and control over their API security, increasing the likelihood of vulnerabilities being exploited.
- Limited monitoring and visibility: Not having a proper system to monitor how APIs are being used can make it hard for businesses to identify and react to security threats or problems quickly.
- Rapid development cycles: The pressure to quickly release new features and applications may result in developers overlooking security best practices, leading to vulnerable APIs being deployed.
- Expanded attack surface: With more APIs in use, there are more potential entry points for cybercriminals to exploit vulnerabilities and gain unauthorized access to sensitive data or disrupt services (image below).

Organizations need to take additional security measures in their API usage (like authenticating APIs instead of merely connecting to them) to reduce their risk exposure.
For example, in one company we analyzed, they had over a dozen active APIs in their HubSpot account. This isn’t uncommon, and it only takes one of these companies to have a breach before your company is at risk.
2. Incomplete knowledge of the security controls in place
Filling out a cyber liability insurance renewal without a comprehensive understanding of the controls implemented (and their extent) can potentially disqualify an organization from insurance compensation in the event of a security incident.
- Cyber insurance providers rely on accurate information about your organization's security measures to assess the risk and provide coverage accordingly.
- When a security breach occurs, they will review your recent renewal policy. They will verify the information provided, such as the implementation of two-factor authentication across all systems.
- If the insurance provider discovers any discrepancies between the stated security controls and the actual implementation, your organization may be deemed to have provided false attestation on your cyber insurance renewal.
This could lead to the denial of compensation claims, leaving you to bear the full financial burden of the security incident.
Whether it's ransomware that shuts down a production line, a business email compromise that redirects a seven-figure payment to a hacker's account, or the exposure of sensitive files and business secrets, these costs can be astronomical.
Your best protection is to align with a recognized cyber framework (NIST CSF at a minimum):
- This helps you identify gaps in your protection that can be addressed to avoid an incident.
- You can share attestation of compliance with customers, your Board, investors, or other stakeholders.
- This can also help protect from regulatory fines and legal judgments.
A lack of proactive effort to identify and remediate risks (or if there’s evidence of C-level awareness of risks, without action) can threaten your coverage.
With the rise in cyber incidents, cyber insurance costs are going up. It’s a bad time to waste that investment.
3. Alert fatigue
Alert fatigue can result in complacency when monitoring threats. This fatigue can arise when security teams are continually bombarded with alerts and false alarms, leading to a decrease in attentiveness and a reduced sense of urgency.
You and your team need to understand that even though it's impossible to block every threat or probe, detecting them all is crucial. Insignificant issues now can escalate into catastrophic problems later if they are not detected and addressed.
In other words (to get back to that baseball metaphor) you can’t afford to miss a single pitch here.
Consider a few ways to make sure nothing is getting past you.
-
Prioritize alerts based on severity and impact.
-
Streamline processes using automation and orchestration tools.
-
Improve alert quality to minimize false alarms.
-
Provide regular training and support for your security team.
-
Lean on cyber partnerships to catch blind spots.
Improving your cyber security “batting average”
Just as Ted Williams honed his skills through practice and patience, organizations can make incremental improvements by concentrating on fundamental areas to enhance their overall security posture.
To push your cybersecurity "batting average" in the right direction, focus on making regular improvements.
This may include strengthening access controls, regularly patching software vulnerabilities, training employees on cybersecurity awareness, and maintaining a proactive approach to threat monitoring and detection.
Companies who want to stay proactive with security will often work with third-party experts. When a major US food manufacturing company reached out to us, for instance, we helped them identify some major blind spots, and gave them the comfort of knowing no pitch would get past them unnoticed. Read our cyber security case study if you’d like to learn more about it.
 Jesse White
Jesse White
VP, Strategic Partnerships Jesse leads the client and business development teams at Katalyst. His experience spans multiple technology platforms and infrastructure. He is skilled at helping customers solve business challenges, navigate market trends and make smarter decisions with disruptive technologies.



